Askfm Reverse Engineering: Getting Threads Back!

So you heared it. Askfm Reverse Engineering! to get back the threads to the web version by creating a web extension that calls the mobile api to show the data and more.
What the heck is askfm ?
Ah Askfm, the good old days when you get back from school and open your askfm account to check these question: which back at the time looked like ‘What is your favourite colour ?, What order do you wear your shoes ? etc…’.
Askfm was something cute when almost few people (those who had opinios about everything) used it, now it became a monster, turned into an ad targeting application with many features that ruined the application : like coins (the first stupid thing), then many more stupid featues and many people used the application the wrong way (you know what I mean if you’re using it now).
Motivation
Probably one important feature which got nuked by askfm is : threads.
Back in time, threads was the best feature, you basically send a question to something with replies inside it, the reply isn’t shown unless the owner publish it with answer. Replying with an image was a thing!
Now askfm nuked it, and made it only available for the mobile users (really!) with huge differences (it’s called chat now):
- Anyone can reply to the question with anything without the permission of account owner!!!
- Can’t reply with images as account owner.
Anyway, I am not here to convince you to leave askfm, I have a history of creating askfm bots and auto_repliers, when I logged into my very old account (which is deleted now btw) I tried to view a thread and I wasn’t be able to do so (had to install the application on my phone).
So I thought it would be a great idea to have some sort of a web extension to just show the questions/replies under a question.
In this blog, I am sharing my journey to do so!
Setup
After a quick research and inspection to the web version of the askfm, I found out that askfm mobile is different from the web version (ofc).
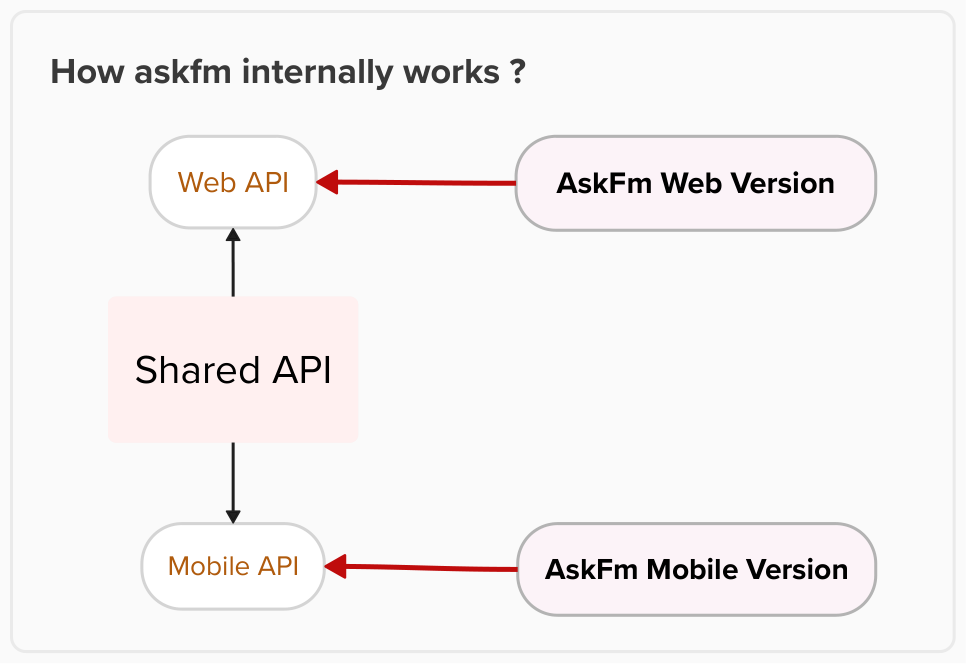
so at first glance, I thought about inspecting the traffic in the mobile application. So I tried many mobile application to inspect the traffic but nothing worked !!.
That’s why I switched to using proxy applications like charles but it didn’t work! (i don’t remember why!).
Lastly found this awesome, game changer, program: HTTPToolKit but this need to run inside a VM, so I installed Genymotion(coz you know, I am lazy)
I wasn’t be able to install the application on the VM on the first try to I had to do some tricks:
- I modified the buildprobs at :
/system/build.propand removed all the VM traces by Genymotion.
Inspecting the Traffic
As you can see below, The API askfm uses is mobile specific. and it uses HMAC for the authorization.
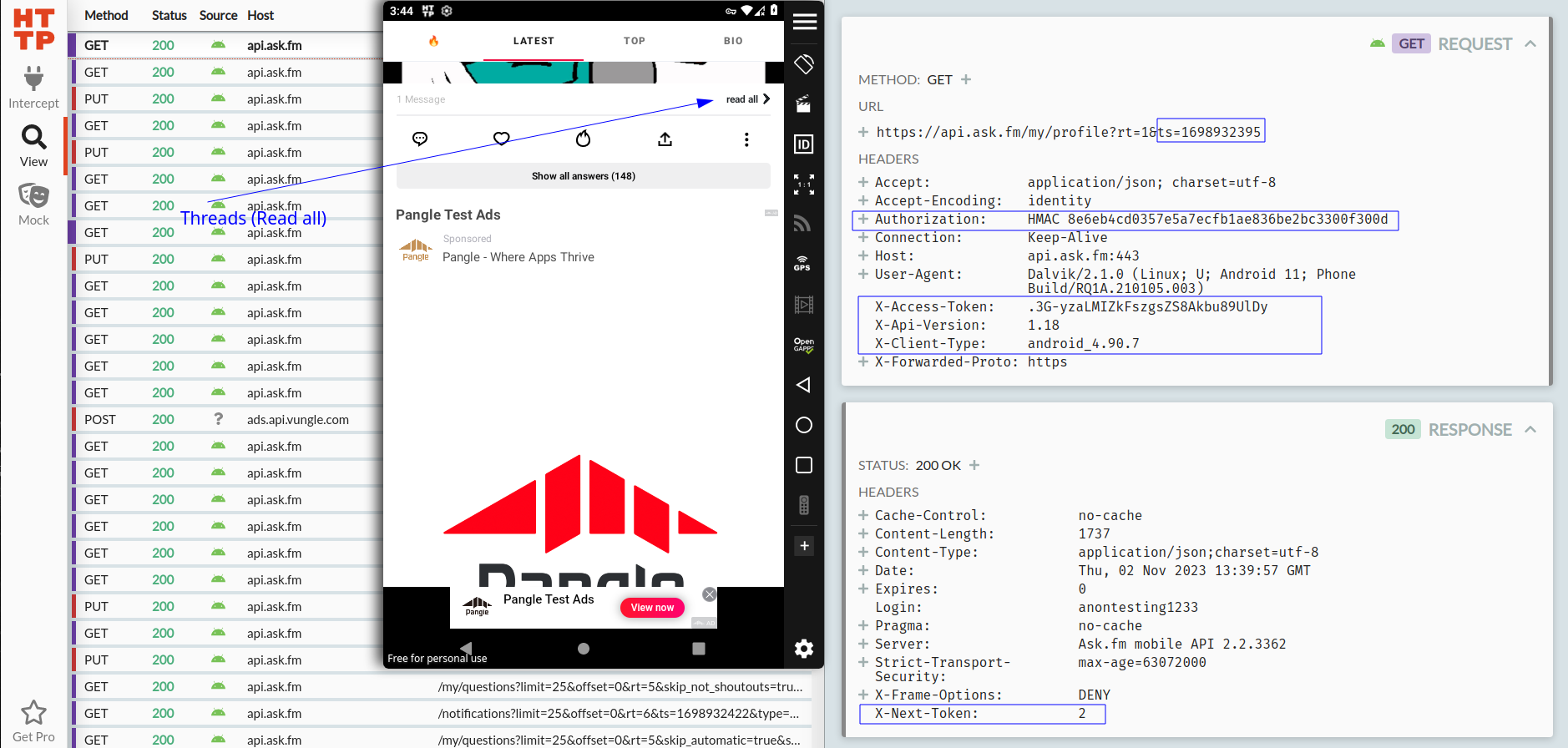
HMAC (Hash-based Message Authentication Code) is a specific type of message authentication code that involves hashing a message with a secret key to produce a fixed-size output, which can be used to verify the integrity and authenticity of the message. HMAC is commonly used for authentication and integrity checking in various security protocols and applications, such as in web services, API authentication, and data transmission.
How HMAC authorization works is simple:
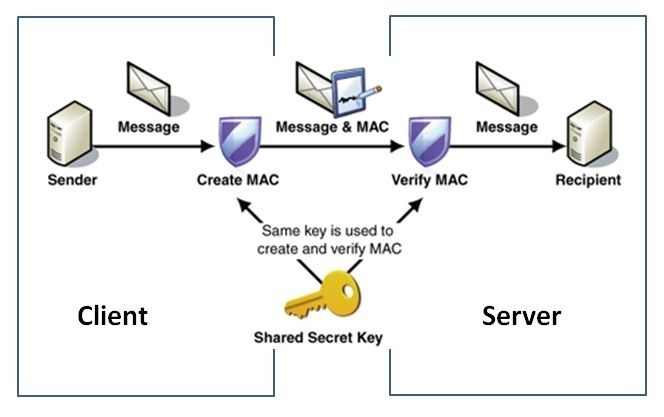
So basically, there are 2 steps that the application does to send a HTTP Request:
- Key Generation : The key should be in the app and the server agrees on using that key.
- HMAC Calculation: The app calculates the HMAC by applying a specific cryptographic hash function (SHA-1) to the message and the secret key. The result of this calculation is a fixed-size hash value which is then send in the headers as :
Authorization: HMAC <hash>
So all we have to do now it just find the KEY and how the app generates the HMAC hash! (easy?).

Decompiling the apk
So you’re still here ?, good because we’re just about to start the interesting part.
What’s an APK you ask ?
APK is a compressed archive file that contains all of the data and resources needed by an application to run on Android device. This mean we can extract it.
For this propose I used Jadx which is a command line and GUI tool for producing Java source code from Android Dex and Apk file, jadx can’t decompile all 100% of the code, so errors will occur.
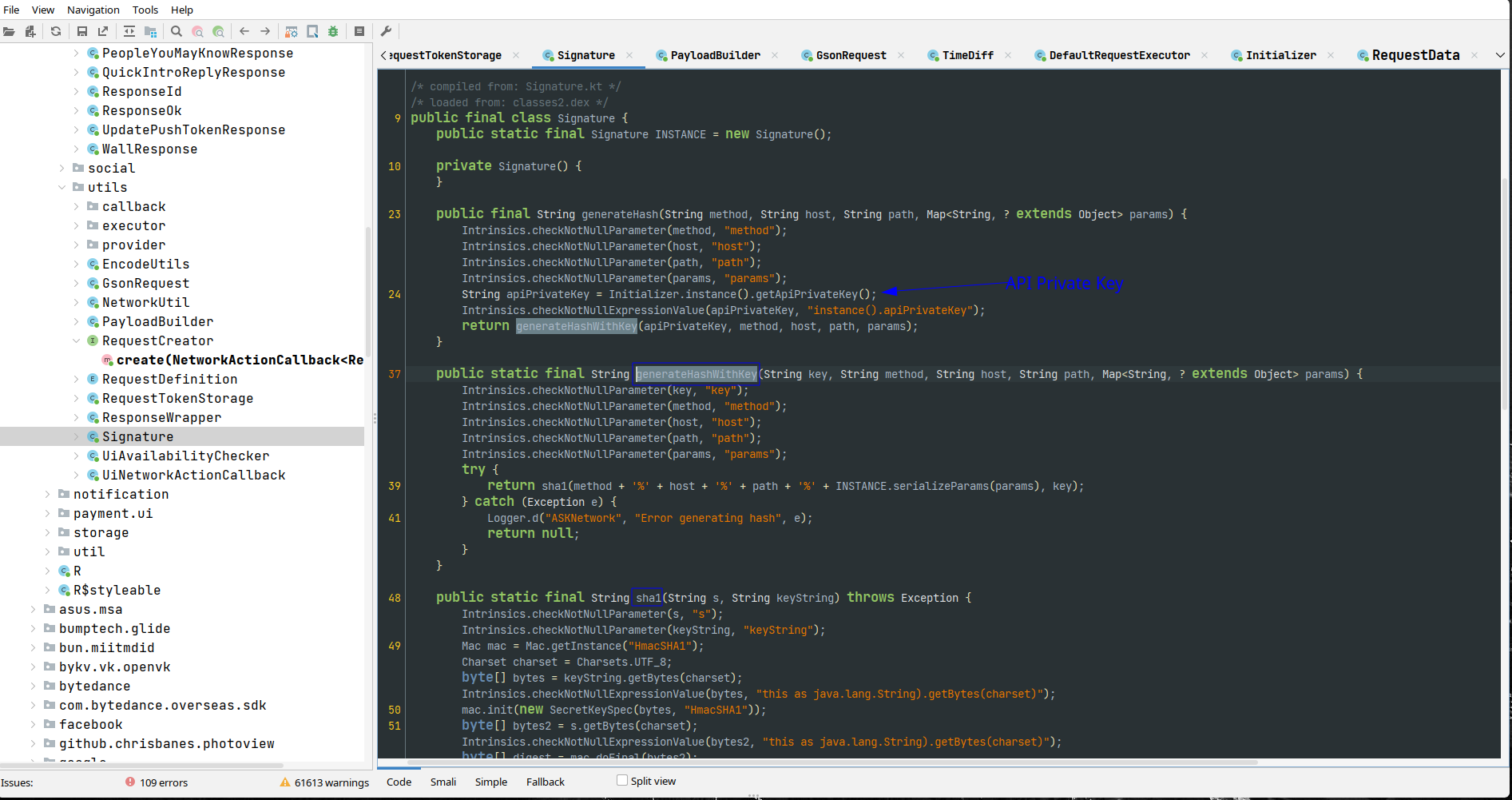
As you can see, I have found the part which generates the HMAC hash.
Digging the code more we’ll find many interesting things:
- The needed headers (which are obvious from the network inspection).
Accept,Accept-EncodingX-Client-Type: maybe used for client identification.X-Api-Version: the API version to use.X-Access-Token: the access token, which is fetched, somehow, separately.
|
|
- Server Params.
|
|
- Request definitions for all the api routes.
|
|
- Parsing the response.
Note that setNextRequestToken: 'X-Next-Token' from the response. Also the timeDiff (probably some way to check the integrity of the request!)
|
|
- The Signature.
Probably, this is the most interesting peice of code, yes you guessed (HMAC hash generation).
Playing around with code has revealed some nasty parts:
|
|
Hmm, now what?
So far so good, let’s recap what we have achieved so far.
- We found the KEY used in the HMAC generation, but a native lib called
ffmpcodecis used to (maybe) perform some string modifications on the KEY. - The HMAC
generateHashmethod uses customsha-1. - The required headers are
X-Access-Token,X-Api-Version,X-Client-Type.
Probably, the hardest thing to achieve here is that the KEY has some sort of native lib to apply some modifications and returns a new string, if you know the new string KEY_NEW, we could you it directly after rewriting the other parts like generateHash.
Decompile, Modifiy, Recompile
We can use the apktool to decode/decompile the apk, then make some modifications, recompile and test.
|
|
After decompiling, the source is converted to samli, samli is a human readable format of the dex code. Take this example:
- Java code looks like this:
|
|
- The dex code, which will most likely contain the hexadecimal sequence:
|
|
- The samli version:
|
|
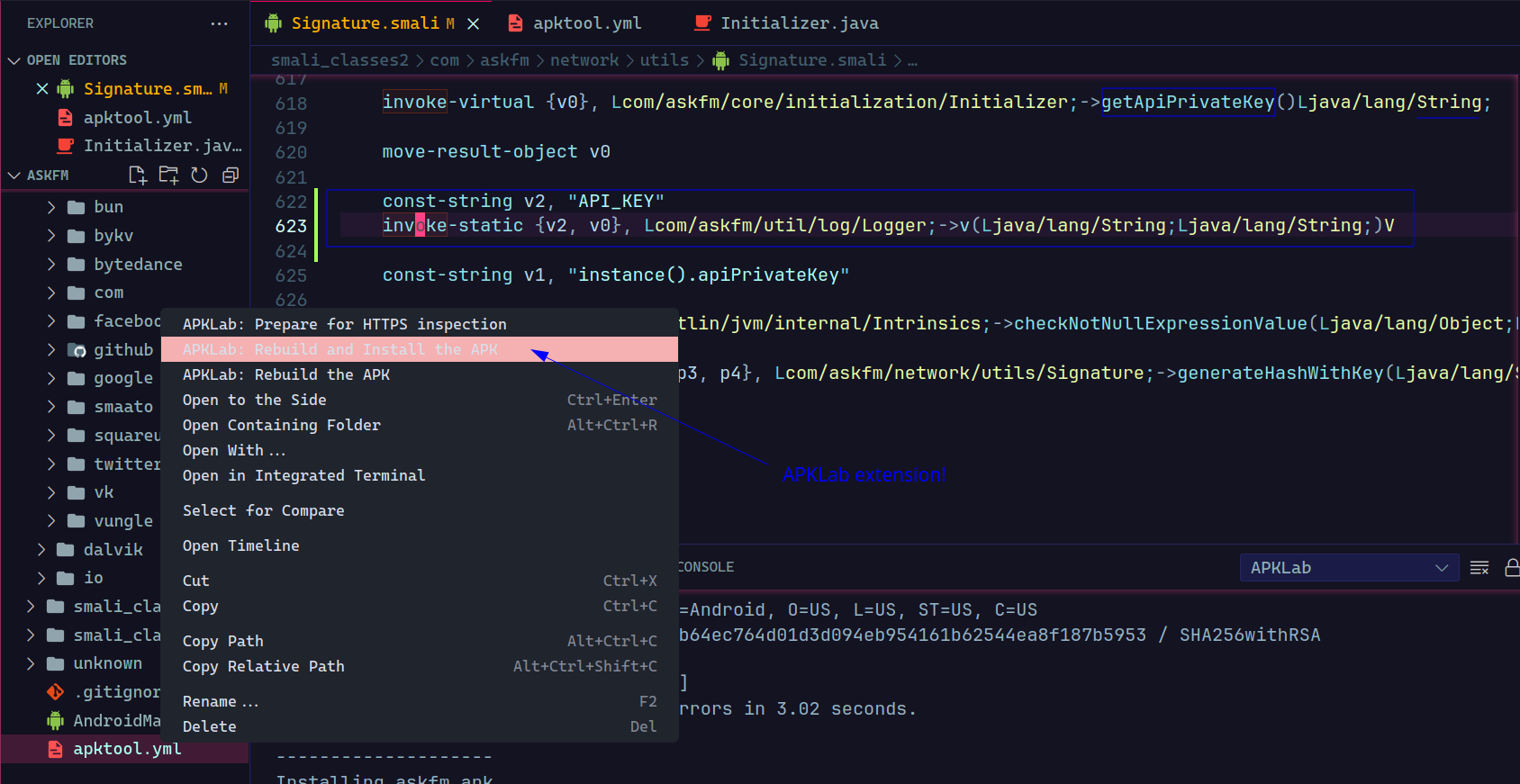
Now let’s modify the file where the apiPrivateKey is called, recompile and install the app. Here I am using APKLab which is a nice VS code extension for android reverse engineering.
Logging
Since I am connecting through adb, it would be obvious to use logcat.
Let’s now get all the logs from askfm : adb logcat | grep askfm
great, no logs :'(
Here are what I found about after some investigations using mobile-security-framework-mobsf:
- The app uses some anti-debugging mechanism.
- I need to dynamically analyse the app in runtime.
Dynamic Analysis
That’s where frida shines, firda is a reverse engineering tool used for dynamic analysis and manipulation of software. It allows developers and security researchers to analyze and modify running applications, helping them understand how the software works and identify potential vulnerabilities. Frida is widely used in the cybersecurity and software development industries.
Here is a great tuturiol, explains basics of reverse engineering + frida:
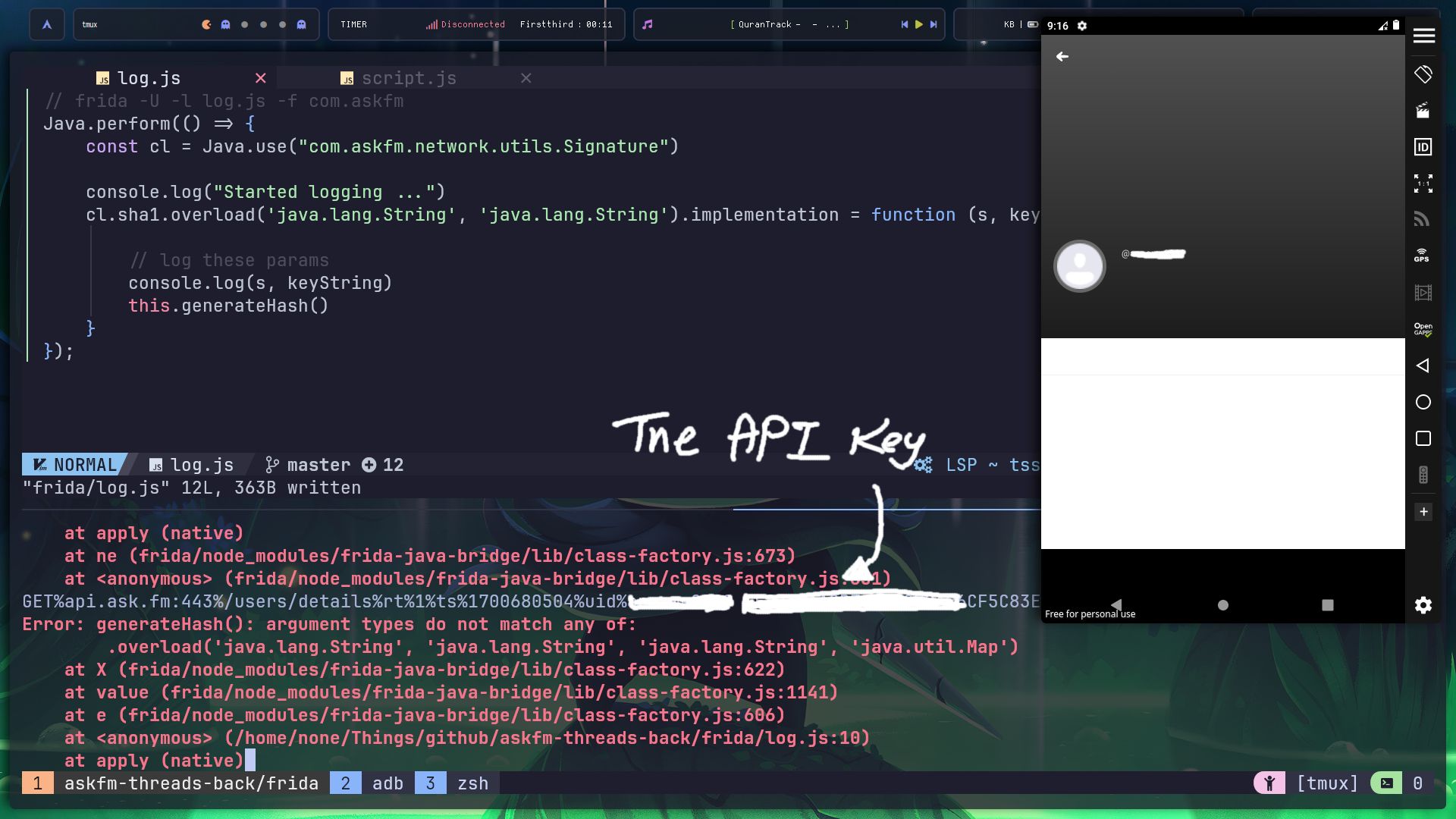
I install frida and hooked up the frida server to the VM. And here’s the script I wrote:
|
|
And finally the key!
With many tries, finally I have logged the key!
What’s next?
After I successfully got the API, I created a web extension to call the mobile APIs, get the data and modify the HTML.
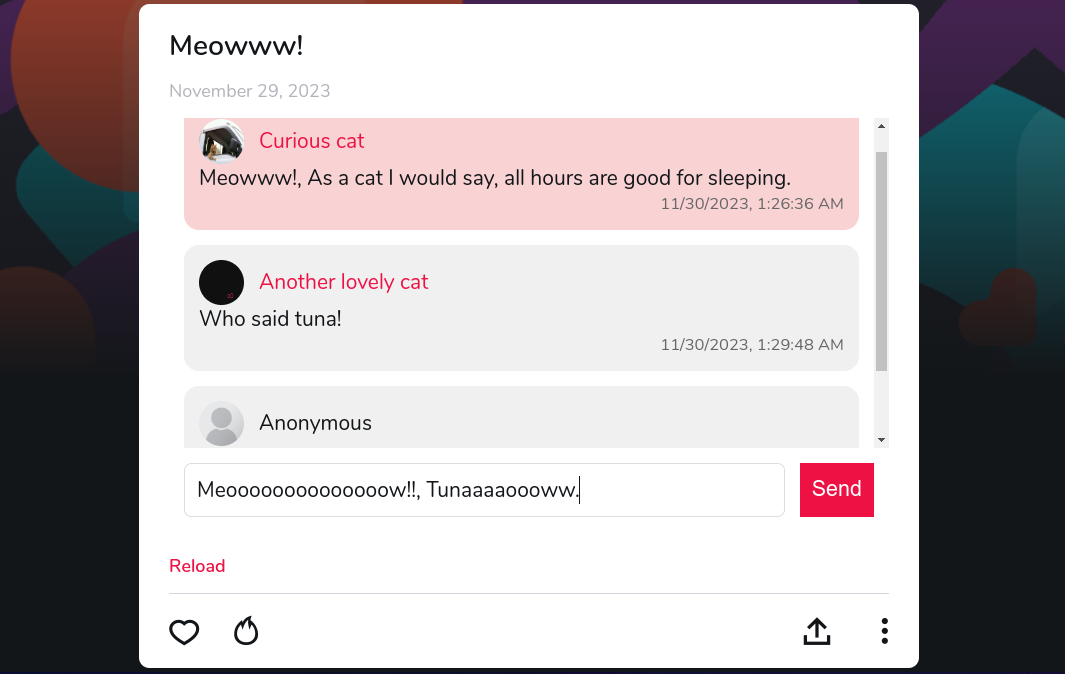
Say Hello :D
Sponsor